This page discusses some essential information and practices for approved researchers of Secure Transfer, Restricted-Use Data Lake (STRUDL) data. Each section has an accompanying video and text is provided as a visual aid. Documents referenced in each video are always formatted in bold and descriptions of each document can be found on STRUDL: Forms. We encourage potential applicants and program participants to reference the STRUDL Handbook for more detail on the full program process.
In Video 3.1, we cover key points of contact for various questions that approved researchers may encounter. In Video 3.2, we cover key security practices approved researchers should implement to ensure that STRUDL data remains secure. In Video 3.3, we review aspects of the STRUDL program that might influence project schedules and monitoring.
Video 3.1 – Secure Transfer, Restricted-Use Data Lake Points of Contact
Overview
In this section, program participants will learn the following:
- Examples of equipment-related (software and hardware) issues, security violations, and other questions that may arise for STRUDL approved researchers.
- Contact information for each of these categories of questions and issues.
What are examples of equipment-related questions?
U.S. Department of Labor (DOL) computer equipment–related questions include those regarding the software installed on the computer equipment and the equipment (hardware) itself. Software refers broadly to the programs or other operating information used by a computer. Hardware refers broadly to the actual device and equipment that allows a computer to perform its functions.
Software questions or issues might involve
- needing a particular software installed to work on a project,
- running into errors or issues with a previously installed program or the current operating system,
- running into errors or issues with access to internal DOL sites and files (note: this is separate from access to the confidential data), or
- running into errors or issues with DOL-provided updates to software and operating systems.
Note: Data analysis software (e.g., R, Python, SAS, and Stata) used to analyze confidential data are accessed via web browser and do not need separate installations. More information will be provided once approved researchers gain access to DOL systems.
Hardware questions or issues might involve
- physical damage to internal laptop parts, such as water damage or damage from a fall,
- issues with the personal identity verification (PIV) card, or
- functioning of laptop screen or keyboard.
What are examples of security violations?
Security violations can take many forms, and the examples we list here are not exhaustive. STRUDL approved researchers should ensure they are up to date on any security trainings required by DOL and are aware of the security stipulations in the required nondisclosure agreement (NDA).
That said, some common types of security violations include
- computing equipment or PIV cards being lost or stolen,
- unauthorized user gaining access to the confidential data, or
- unauthorized user viewing or receiving information derived from the confidential data that was not cleared by the STRUDL team through the required disclosure review process (see Video 2.1 and its associated text for details).
To ensure DOL can respond appropriately, as soon as a researcher becomes aware that a violation has occurred, the researcher should report this breach immediately via the procedures outlined in DOL security trainings and the DOL intranet.
What are examples of other questions approved researchers might have?
Approved researchers in STRUDL might also encounter questions or issues regarding
- systems used for accessing STRUDL data,
- information about the confidential data, including collection or processing methodology,
- information about applying disclosure control methods prior to or during the disclosure review process, or
- questions for which the point of contact is unclear.
Who should approved researchers contact for each of these types of questions?
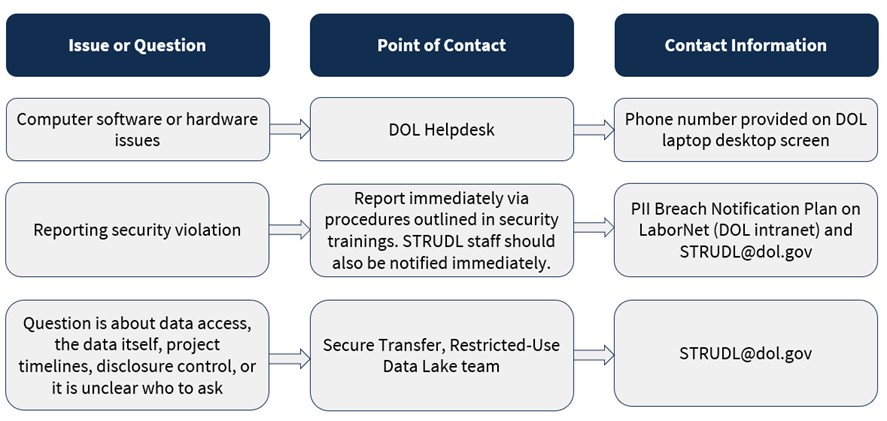
As depicted in Figure 1, there are three main categories of issues or questions approved researchers may encounter. The primary points of contact and recommended contact information for each type of question are as follows:
- Computer software or hardware issues should be reported to the DOL Helpdesk. The Helpdesk phone number can be found on the desktop and lock screens of the DOL-provided laptop.
- Security violations should be reported immediately via the procedures outlined in the annual DOL security trainings, including the PII Breach Notification Plan that can be found on LaborNet (the DOL intranet). STRUDL staff should also be made aware of all security violations immediately after they occur.
- Other questions, including questions about the data access, the data itself, project timelines, disclosure control, or questions where the point of contact is unclear, can be directed to the STRUDL team via STRUDL@dol.gov.
Video 3.2 – Secure Transfer, Restricted-Use Data Lake Security Practices
Overview
In this section, program participants will learn about the following:
- Keeping computer equipment and PIV cards secure
- Keeping data secure
Please note that all these practices are recommended, and in some cases required by DOL and STRUDL policies, but the lists here are not exhaustive. STRUDL approved researchers should ensure they are up to date on any security trainings required by DOL and that they are aware of the security stipulations in the required non-disclosure agreement (NDA).
How can approved researchers keep physical Department of Labor (DOL) resources, like laptops and PIV cards, secure?
Here are some practices that can help maintain the security of the DOL equipment and PIV card:
- Store the DOL laptop in a secure location within your workspace.
- If leaving your workspace for a long period of time (i.e., going on vacation if you work from home), consider taking additional precautions regarding the security of the DOL laptop (e.g., locking it in a secure location).
- When stepping away from the DOL laptop, lock it or log out and remove the PIV card.
- Store the PIV card in a secure location and separate from the DOL laptop.
- If laptops or PIV cards are lost or stolen, report this security breach immediately via the procedures outlined in DOL security trainings.
How can approved researchers keep data secure?
As a reminder, STRUDL approved researchers are not allowed to share any results or information derived from the confidential data outside of DOL systems, or with anyone outside of the approved project team, until that information has undergone disclosure review by STRUDL staff (see Video 2.1 and its associated text for more details).
To avoid this type of security violation, STRUDL approved researchers should
- never access confidential information on a DOL laptop while nonapproved individuals (including roommates, partners, coworkers, etc.) are in the room,
- never discuss or share (even informally) results or features of the data (including the presence or absence of variables and records) with nonapproved individuals, and
- always report data security breaches immediately via the procedures outlined in DOL security trainings.
Video 3.3 – Secure Transfer, Restricted-Use Data Lake Project Monitoring
Overview
In this section, program participants will learn about the following:
- Monitoring approved project schedules
- Adding researchers to the project
What are key timelines approved researchers should be aware of when monitoring approved project schedules?
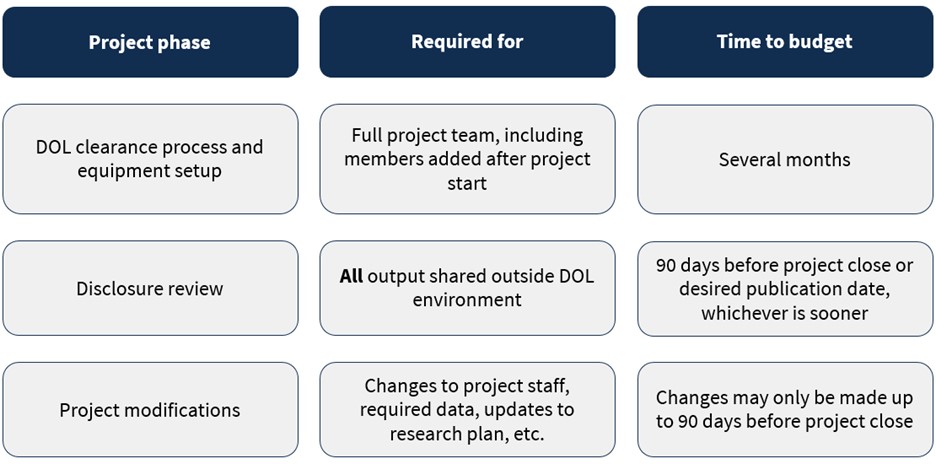
There are several key timeline elements that STRUDL approved researchers should be aware of while monitoring their project schedules, including the aspects of the project for which these elements are required and the time that should be budgeted. As depicted in Figure 2, approved researchers should budget at least
- Several months for the full project team (including any member added after the project starts) to go through the DOL clearance process and set up equipment;
- 90 days before the project close (or 90 days before the desired publication date, whichever is sooner) for all output shared outside the DOL environment to undergo the disclosure review process; and
- 90 days before the project close to make any project modifications, including changes to project staff, required data, or updates to the research plan.
For more information on the disclosure review process, see Video 2.1 and its associated text. See the STRUDL Handbook for more information about what is required for submitting the disclosure review package.
How can approved researchers be added to an existing project?
Adding researchers to the project is a specific type of modification covered by the STRUDL Project Modification Request form (see description on STRUDL: Forms). Principal investigators of the approved STRUDL project should submit this form to STRUDL@dol.gov, and if the additional researchers are approved, DOL staff will reach out to initiate the clearance and access process, including signing the STRUDL nondisclosure agreement. (This process is described further in Video 1.2 and its associated text). Please note that, as described above, new researchers are subject to a waiting period while their clearance and access are processed.
